Introduction
In today’s digital world, safeguarding critical infrastructure is a top priority for governments, businesses, and individuals. Operational Technology (OT) forms the backbone of essential services such as energy, transportation, healthcare, and manufacturing, among others. As systems connect more and rely on digital tech, they are more at risk of cyber threats. In this blog we’ll look at Lessons Learned from OT Security Incidents.
In the past, we have seen many times when OT systems were hacked, causing big problems and sometimes very bad outcomes. These incidents serve as sobering reminders of the urgent need to bolster the security measures surrounding critical infrastructure.
Understanding Operational Technology (OT) Security
Operational Technology encompasses the hardware and software used to monitor and control physical processes in industries like energy, transportation, and manufacturing. Unlike traditional IT systems, OT focuses on real-time control and automation, making it uniquely vulnerable to cyber threats.
The Landscape of OT Security Incidents
The OT security landscape faces a growing threat as cyberattacks target critical infrastructure, potentially causing physical disruptions and safety hazards. Here is the list of incidents which took place and thus transformed the new landscape of OT Security.

|
Attack Name |
Location |
Root Cause |
Method of Attack |
Damage Done |
Reference |
|
Stuxnet(2010) |
Iran |
vulnerability in SCADA systems |
Worm, exploiting zero-day vulnerabilities |
Disruption of uranium enrichment centrifuges |
|
|
Triton(2017) |
Saudi Arabia |
Targeted vulnerability in safety instrumented systems (SIS) |
Malware injection targeting Schneider Electric’s Triconex controllers |
Attempted sabotage of industrial safety systems |
|
|
Ukraine Power Grid(2015) |
Ukraine |
Cyber-espionage group targeting SCADA systems |
Remote access through phishing, followed by malware deployment |
Widespread power outages affecting thousands |
https://blog.isa.org/lessons-learned-forensic-analysis-ukrainian-power-grid-cyberattack-malware |
|
Ransomware Attack on Colonial Pipeline(2021) |
USA |
Software Vulnerability |
Ransomware Deployment |
Temporary Fuel Supply Disruption |
https://www.nytimes.com/2021/05/12/business/colonial-pipeline-ransomware.html |
|
Industroyer (2016) |
Ukraine |
Targeted SCADA systems |
Malware exploiting vulnerabilities in power grid protocols |
Temporary disruption of power distribution |
|
|
Maroochy Water Services Attack(2000) |
Australia |
Insider Sabotage |
SCADA System Manipulation |
Sewage Overflow |
https://www.abc.net.au/news/2019-07-10/maroochy-water-hacking-incident-damage-undisclosed/11292150 |
|
CrashOverride(2016) |
Ukraine |
Targeted Ukrainian power grid |
Malware designed to manipulate electric grid systems |
Disruption of power distribution |
https://www.dragos.com/resource/crashoverride-analyzing-the-malware-that-attacks-power-grids/ |
|
BlackEnergy(2015) |
Ukraine |
Targeted SCADA systems |
DDoS attacks and malware |
Major power outages, system disruptions |
https://www.kaspersky.com/resource-center/threats/blackenergy |
|
Dragonfly(2014) |
Worldwide |
Targeted energy sector |
Spear phishing, watering hole attacks |
Data theft, disruption of energy operations |
https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/dragonfly-energy-companies-sabotage |
Shamoon(2012) |
Saudi Arabia | Targeted Saudi Aramco | Disk-wiping malware | Destructive data loss, temporary shutdowns | https://en.wikipedia.org/wiki/Shamoon |
Lessons Learned from OT Security Incidents
Lessons Learned from OT Security Incidents are the insights gained from analyzing cybersecurity breaches or compromises within Operational Technology (OT) systems, aiming to improve future security measures and strategies.
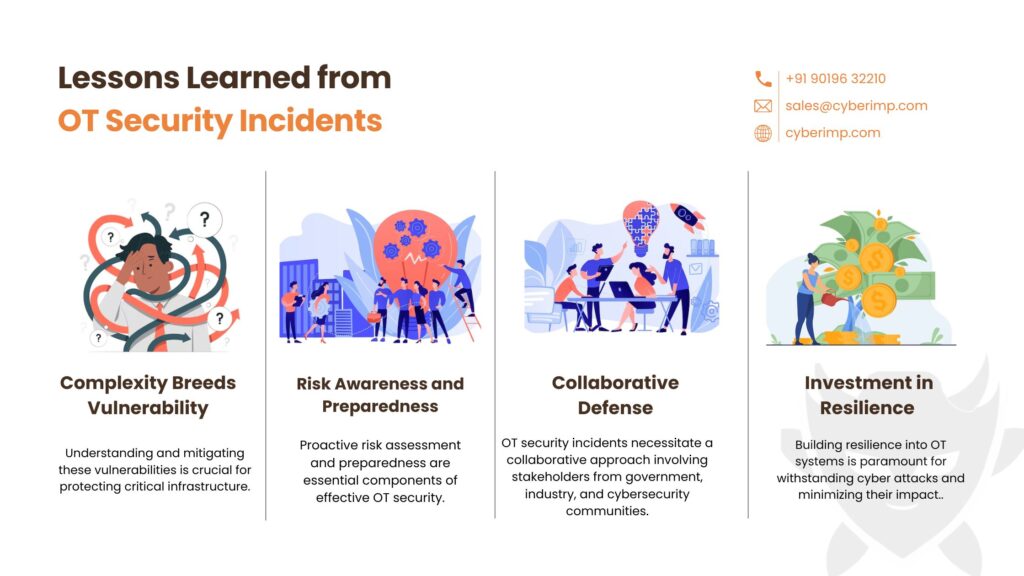
1. Complexity Breeds Vulnerability: The complexity of OT systems, often composed of interconnected devices and legacy equipment, introduces numerous entry points for cyber attacks. Understanding and mitigating these vulnerabilities is crucial for protecting critical infrastructure.
2. Risk Awareness and Preparedness: Proactive risk assessment and preparedness are essential components of effective OT security. Organizations must identify potential threats, assess their impact, and implement appropriate safeguards to mitigate risks.
3. Collaborative Defense: OT security incidents necessitate a collaborative approach involving stakeholders from government, industry, and cybersecurity communities. Sharing threat intelligence, best practices, and lessons learned can enhance the collective defense against cyber threats.
4. Investment in Resilience: Building resilience into OT systems is paramount for withstanding cyber attacks and minimizing their impact. This includes implementing redundancy measures, disaster recovery plans, and robust incident response capabilities.
Looking Ahead: Strengthening OT Security Posture

1. Security by Design: Incorporating security considerations into the design and development of OT systems is essential for building robust defenses against cyber threats. Security must integrate at every stage of the system life cycle, from secure protocols to access controls.
2. Continuous Monitoring and Adaptation: Adopting a proactive approach to OT security involves continuous monitoring for anomalies and potential threats. Organizations must remain agile and adaptable, responding swiftly to emerging cyber threats and evolving attack vectors.
3. Investment in Training and Awareness: Educating OT operators and employees about cybersecurity best practices is critical for mitigating risks posed by human error and insider threats. Training programs should emphasize the importance of vigilance, adherence to security protocols, and incident response procedures.
4. Regulatory Compliance and Standards: Compliance with regulatory requirements and industry standards can serve as a foundational framework for OT security. Adhering to established guidelines helps ensure a baseline level of security and fosters a culture of accountability within organizations.
Conclusion
We understand the cyber is important in the convergence and innovation plays a critical role in securing the cyber Physical system in the era of 4.0 and Operational Technology (OT) security incidents pose significant challenges to the resilience of critical infrastructure. Lessons Learned from OT Security Incidents can improve security and prevent cyber attacks by studying past events and learning from them as did. Protect your important systems by working together, being proactive about risks, and following security guidelines. These threats to operational technology security are constantly changing.



